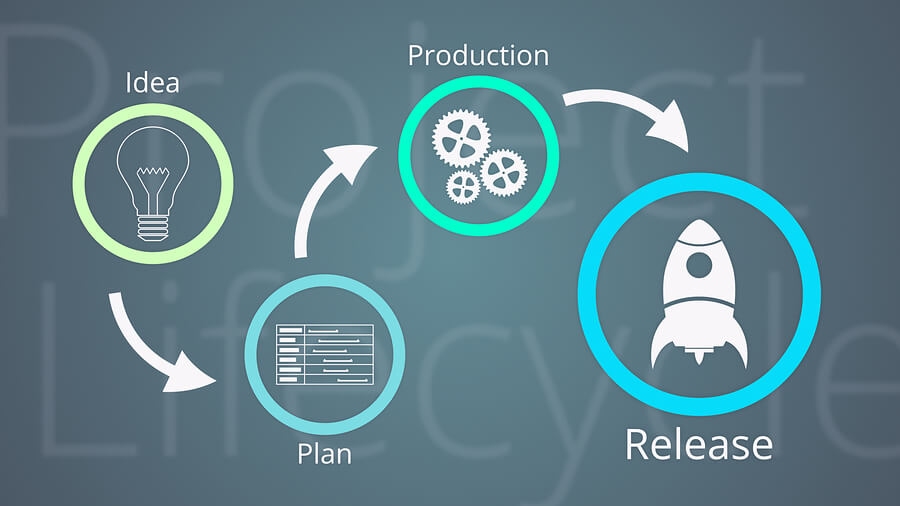
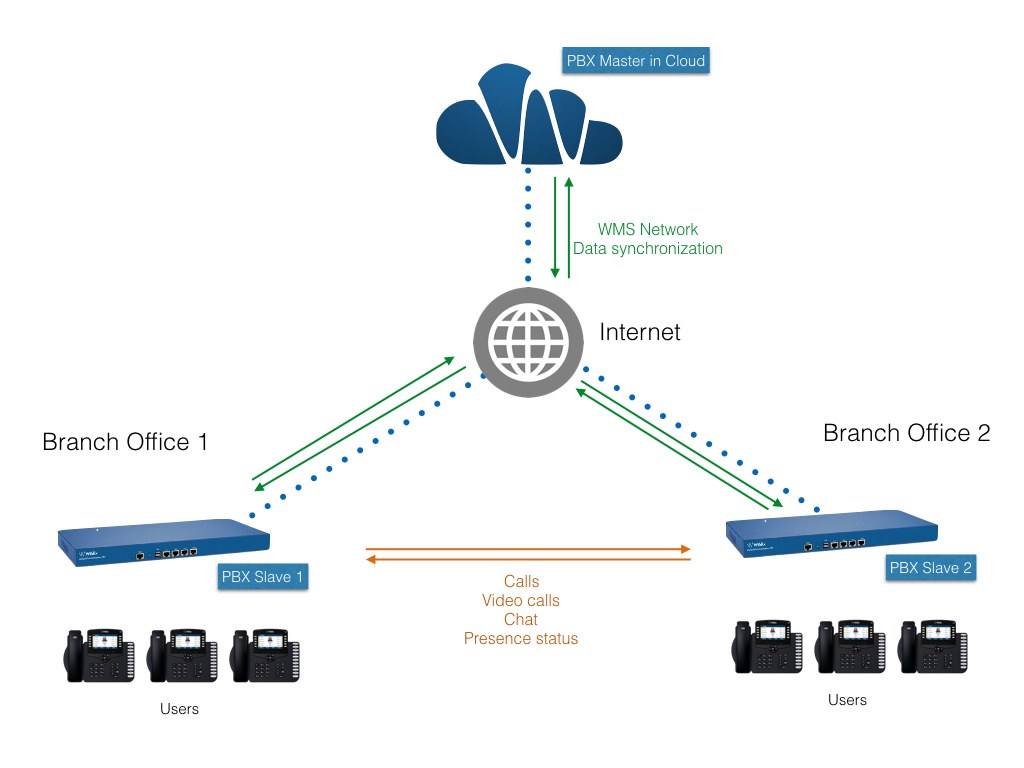
Deployment Planning
In this blog article I will provide some best practices for deployment planning that our UC platform will need, to work as expected. When a new UC system is installed, users will need to spend a considerable amount of time and resources learning