How Two-Factor Authentication and Single Sign-On improve Security?

 Let’s explore how two-factor authentication and single sign-on mechanisms are being used for improving security.
Let’s explore how two-factor authentication and single sign-on mechanisms are being used for improving security.
Two-Factor Authentication introduces an additional security layer to protect accounts whose password has been compromised (for example, in case the password has been stolen). After the usual login and password check, the system will always ask for a security code.
The security code is generated either in real-time (by the authentication system) and sent over SMS, email, or via applications such as Google Authenticator or Microsoft Authenticator.
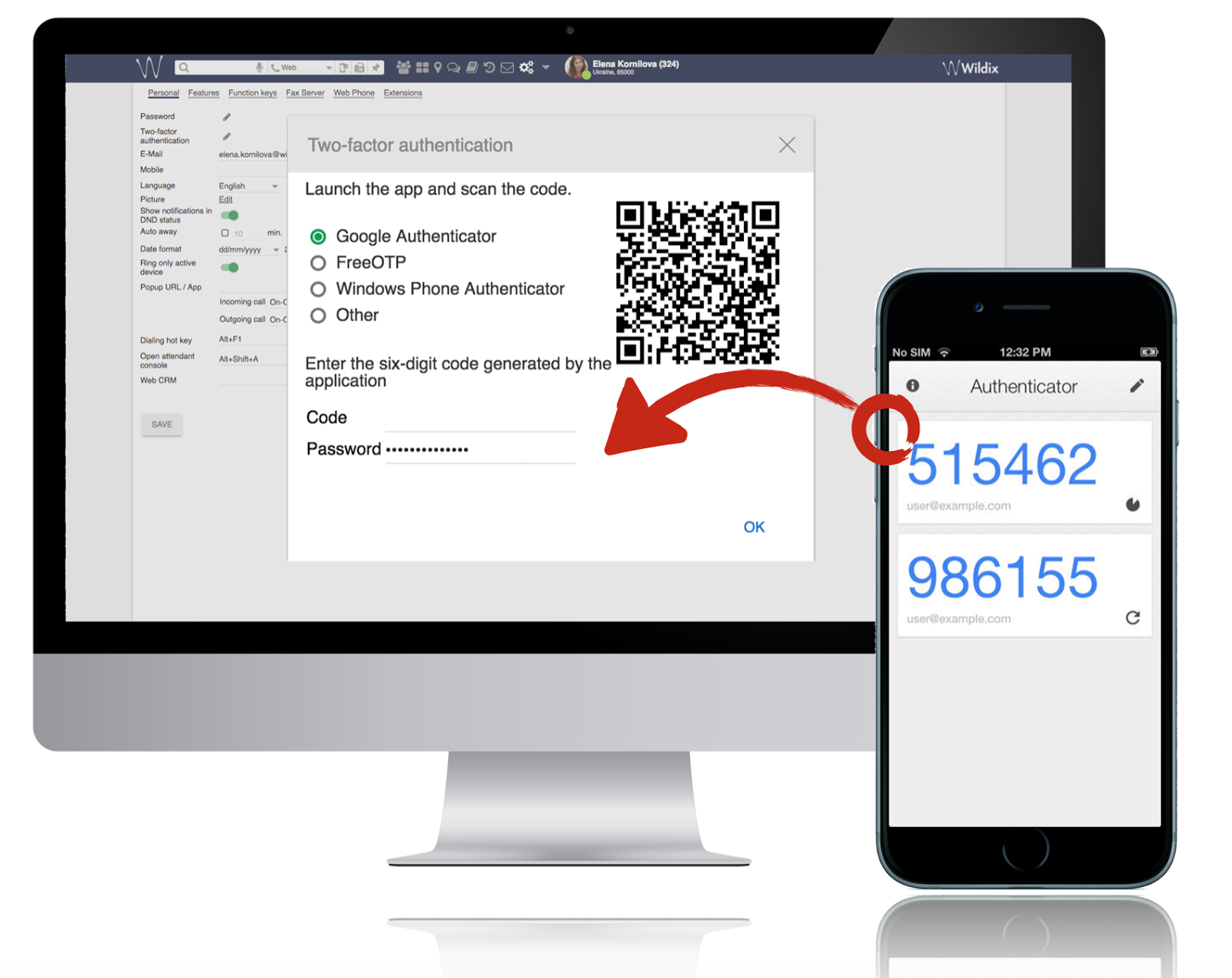 The security code request makes it impossible for an attacker, who only has the stolen password, to access the system.
The security code request makes it impossible for an attacker, who only has the stolen password, to access the system.
Most of these applications, for example Google Authenticator, support both the HOTP (https://en.wikipedia.org/wiki/HMAC-based_One-time_Password_Algorithm) and TOTP (https://en.wikipedia.org/wiki/Time-based_One-time_Password_Algorithm) algorithms for generating one-time passwords.
With HOTP, the server and client share a secret value and a counter, which are used to compute a one-time password independently on the side of the client and server. Whenever a password is generated and used, the counter is incremented on both sides, allowing the server and client to remain in sync.
TOTP uses the same algorithm as HOTP with one major difference: The counter used in TOTP is replaced by the current time. The client and server remain in sync, as long as the system times remain the same. This synchronization can be done by using the Network Time protocol.
The secret key (as well as the counter, in the case of HOTP) has to be relayed to both the server and the client at some point. In the case of Google Authenticator, this is done in the form of a QRCode encoded URL.
Single Sign-On
The best solution to enforce security is to reduce the number of passwords that a user must remember.
Passwords, especially secure and complicated ones, are hard to remember, and usually end up being saved on paper, especially if the user needs to remember a large number of them.
Using single sign-on with an existing system, which can authenticate the user, brilliantly solves this problem. When implemented, it prompts the user to enter the credentials to access the existing system and, if configured, the two factor authentication security code.
In many cases, for example when using a browser, if there is already an active session, the user will just need to authorize the Unified Communication application’s logon access, instead of enter credentials again.
So, whenever possible, it is better to authenticate against an existing system, such as a mail or directory server. A few popular examples are Gmail, Office 365, or Microsoft Active Directory. This feature not only makes the system more secure, it also makes things easier for all users.